Lather, Rinse, Repeat - the Never Ending Cycle of Good Cybersecurity
Like your doctor says when you go in for that annual physical you skipped: eat more veggies, get more exercise, sleep well. The same holds true for good cybersecurity - it's the repetitive, boring stuff that often matters most.

There is no question that cybersecurity is a dynamic, ever changing field. There are new challenges every day, and novel attack vectors occur all the time. The following two comics, written 14 years apart, illustrate this nicely.
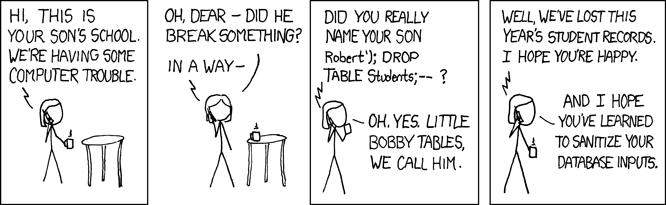
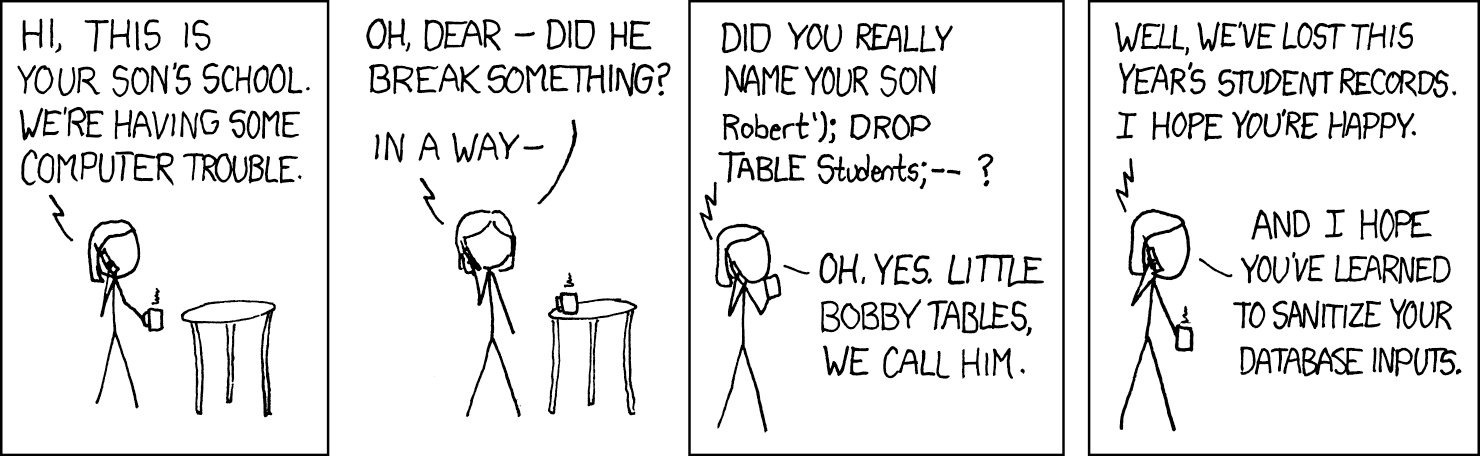
Randall Munroe everyone, one of the best, this comic is from October 2007.

Sharp eyed readers, especially those who have mastered the zoom function on their browser, will note that the second comic even pays homage to the first in the lower right. Even more of you will notice the similarities in the vulnerability exploited for the gag to work. For those who don't know, both approaches actually work for their specific targets, and both are essentially the same issue: programs that do not do any sort of validation checking on the inputs allowed from users. Those of you who are more forward thinking will note that while there was actual "code" involved in the older exploit, natural language was all it took to get the AI system to behave poorly. (But don't worry, this isn't an "AI is bad!" post, these cartoons are just an illustration)
Those Who Refuse To Learn History Are Doomed To Repeat It
The difference in these two illustrations is the attack surface, the actual attack is the same. This suggests that, while perhaps we learned to validate inputs against databases, we didn't make the larger leap to realize we need to validate inputs against any system.
There is a reason why the OWASP Top 10 application security risks only had 3 new entries in the top ten between the 2017 and 2021 revisions: often the attacks remain the same, it is the systems the attacks are performed against that seems to change. (Is that an oversimplification? Sure, but that doesn't mean it isn't also true.)
Here's another example. In 2021 one of the most famous ransomware breaches happened to Colonial Pipeline. Point of entry into the environment was an out-dated VPN solution that didn't require MFA authentication. The CEO of this company was hauled up in front of congress - both the house and senate - and explained this to the world.
In 2024, one of the largest breaches to hit the public eye was the breach of Change Healthcare, a subsidiary of United Health Group. Go ahead and guess what the point of entry was. No really, guess. I'll wait. (If you need a hint, read the previous paragraph again)
Wash Your Face, Brush Your Teeth, Clean Your Lenses
One of the tricks to good cybersecurity, if you can call it that, is to make it routine. Just like your bedtime hygiene routine, the habit of doing security right every day cannot be understated. Whether you're protecting yourself or you're protecting an entire organization, this is the stuff that puts you in the best position to maintain a good security posture.
From my perspective there are three fundamental cybersecurity "routines" that need to be baked into your world, whether your scope is for yourself or for a Fortune 50 enterprise.
Patch Often, and Migrate Before End of Support
A frighteningly large number of attacks still rely on patchable vulnerabilities that are more than 6 months old. CISA published an advisory looking at 2022's top routinely exploited vulnerabilities. 7 of their top 12 were Common Vunerabilities and Exposures (CVEs) dated before 2022, with one from 2018 included in the list. The next 30 in the list include vulnerabilities from as far back as 2017.
More than 4% of deployed Windows "desktops" are running out of support Windows versions. For perspective, only about 15% of desktops run MacOS, and less than 5% runs Linux. Let's not even start in on the out-of-date versions of Android out there.
Keeping your software up to date and patched is one of the most important routines you can have to keep your environment safe.
Configure Securely
How many massive breaches have happened because a cloud database wasn't secured properly? How many because someone chose to use the default username and password? Or because the dev environment wasn't secured well, and someone was able to use that info to hack the prod environment?
We have a perfect example in the recent spate of Snowflake related breaches. Snowflake offered multi-factor authentication (MFA) as an option to administrators, but offered it in such a way that wise admins would have used their single sign-on (SSO) solution to proxy all logins to the environment except for a few well controlled and necessary ones. However we saw major enterprise after major enterprise failed to do so, leaving their data vulnerable.
More and more solution providers are requiring security in their *aaS environments, and they're providing good tools to do so. But as the administrator of that environment you need to take responsibility for ensuring those capabilities are turned on and working.
Gone are the days that even the home tinkerer should expect to get things running without https, and without needing to authenticate before accessing their test systems. Even the ubiquitous Raspberry Pi ecosystem has done away with the default username and password they relied on since their inception.
This includes making sure good logging is in configured and being collected (if you're just you) and monitored (if you're any size organization at all).
Manage Identities and Access
For the home user this comes down to three rules:
- Use a password manager
- Make unique, long, strong passwords for each login
- Enable MFA whenever it is offered
For the cybersecurity professional, we need to add a few things to this list:
- Enable MFA whenever
it is offeredfeasible - Deploy SSO for everything you can (and enable MFA for it)
- Practice the principle of least privilege - only give access that is needed
- Practice role-based access control (RBAC)
- Don't allow shared logins
- See 7.
- See 8.
- Reread the list and make sure you did all of it
Yes, it is a list, but it is critical. Business email compromise and many other attack vectors are significantly impeded by this list. Many of the compromises of US water treatment facilities would have been thwarted by this list. The compromise of Colonial Pipeline and many others would also have been harder to achieve if not completely stymied.
But Wait, There's More!
Well, of course there is. Good security is a complicated journey, one that certainly has a beginning, but no definable end. These three recommendations, if turned into absolute habits, will put you on a good footing for a high quality cybersecurity program, whether for your own uses or the organization that employs you. Just don't stop with this list, keep improving. Keep tweaking, and keep updating. You're on the right path.

