Powerful Yet Overlooked - DNS as a Security Solution
Almost nothing you do online works without DNS. It is ubiquitous. But have you ever thought about DNS as part of your security program? Controlling how it is used can make a significant impact on your environment.
For both personal and professional networks, the Domain Name System (DNS) is one of those parts of our online lives that are often just taken for granted. Unless you're an IT worker you likely don't give DNS a second thought in your daily life, it just works quietly in the background making sure that your online world works. This ubiquitous part of your world can be a powerful tool for keeping you secure, or a difficult to counteract security weakness.
DNS TLDR
Every time you go to a website you use a Universal Resource Locator (URL) to get there. (Not sure what a URL is? It's often in the form of "www.website.com/directory/file" or the like) DNS is the system that translates that URL to an IP address. It's effectively the "phone book" for the Internet: you look up the company by name and it gives you the "phone number" to call to talk to them.
That service only works if your computer/phone/etc. knows what IP address the DNS service is running on. Fortunately, this is generally provided to your devices through another protocol called the Dynamic Host Configuration Protocol (DHCP). DHCP is what gives your device an IP address when it connects to the network. Your cell phone gets one from your cellular provider, and your home router gets one from your ISP. Your router/firewall/WiFi system at home then uses DHCP to give your devices IP addresses every time they connect. By default they share the DNS servers they got from the ISP's DHCP information. So every time you look up a URL you're generally asking your ISP's DNS servers to answer for you.
This is just skimming the surface of DNS, but should be enough background for our purposes today, but if you want to understand DNS better you could do far worse than starting with Wikipedia's article on the topic.
Dirty DNS Deeds, Done Dirt Cheap
The malicious use cases for DNS really fall into one of two categories that we want to protect ourselves against.
Impersonating Legitimate Systems
To put this one in telephone terms: what if I got into your phone and changed the phone number you have saved in the entry for your bank. Now the next time you try to call your bank you are actually calling me, letting me impersonate your bank. DNS hijacking is the Internet equivalent of changing up the phone numbers in your address book.
Enabling Communication With Malicious Infrastructure
Even malware uses DNS. One of the reasons they do is that when the authorities find their existing infrastructure and shut it down the "bad guys" can fall back to other infrastructure by changing the DNS entries for accessing their systems. If they hard-code IP addresses into their malware payloads then once their systems were taken offline they'd have no way to easily reconnect to your compromised systems.
These two categories cover a wide swath of possible issues that are critical to the safe functioning of anything we do online. There are plenty of things that the major players in DNS infrastructure do to minimize these issues, but there are still steps that you can take for your own environment, whether that's home or work, to add layers of protection for low effort and low (or no) cost.
Simple and Effective Countermeasures
There are two steps I encourage both home and corporate IT resources to set up to protect against these DNS related dirty deeds.
Web Proxy/DNS Provider
The first step is to replace "regular old" DNS with your own trusted solution. For corporate users, this is generally a web-proxy solution such as Cisco Umbrella or Zscaler. These solutions can not only block malicious DNS activity, but "travel with" your remote workers laptops. They can further be used to restrict access to URLs inappropriate for most work environments, such as this blog.
For home users I recommend the consumer level version of tools like Umbrella - OpenDNS, or for more advanced users, combining that with Pi-hole. OpenDNS works much the same as Cisco Umbrella. You can configure your entire network to use that as DNS by updating your firewall's DNS settings - follow the instructions on the OpenDNS website to set that up. You can also install their DNS agent on your mobile devices so you're protected outside your home as well.
More advanced home users who want to install Pi-hole will end up with a slightly more advanced setup, but Pi-hole does a good job of blocking advertising URLs better than these other solutions do, and as malicious advertising is a legitimate attack vector of concern, this is a valuable security option.
Using a DNS service provider who blocks URLs that are identified as malicious is a powerful security tool for very little effort.
Disable DNS Requests From Your Network That Don't Use Your Settings
This one will likely require some exceptions, but stick with me here. Just because you set up OpenDNS or the like for your actual computers, and your at home firewall (or in corporation DNS/DHCP server) is configured to use those tools, it doesn't mean that I can't override that setting and make a rogue DNS request, especially if I'm a malicious piece of software. To combat this, you want to put in a firewall rule that blocks all outbound DNS traffic that doesn't originate from you DNS server(s) and isn't destined to your DNS provider. This can break things, so be prepared to do some testing and troubleshooting. For example, if you work from home with a company computer your DNS settings may conflict with the company's, and you'll have to resolve that in your firewall rules. For that very reason I recommend giving yourself a few days minimum between implementing a DNS provider service and then blocking all other DNS traffic outbound.
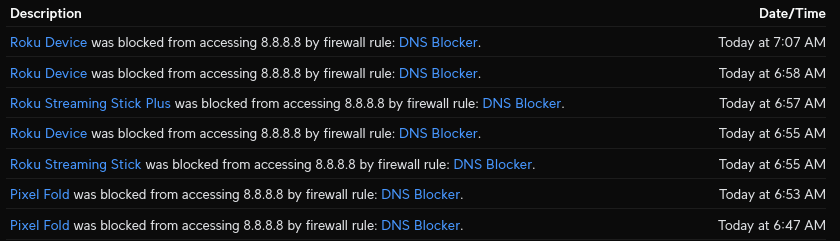
Blocking DNS that doesn't use you preferred DNS solution can make it harder for malware to talk to bad actors infrastructure. While this may be slightly challenging for home networks, companies and corporations should see this as low-hanging-fruit.
What These Suggestions Can't Do
While these suggestions are helpful on a network you control, or on a full-fledged computer you own, they aren't very helpful for your mobile devices on cellular or on other people's networks. Of course that doesn't mean you can't, or shouldn't connect to cellular and 3rd party networks, it just means you'll have one less layer of security when you do so.
Making sure you know what you're talking to on the Internet is an important step to secure Internet communications. Hopefully after reading this you won't take that for granted, but will actively work to ensure your own communications are that much safer when you take control of your DNS options.

