Quickly Cutting Through the New Vulnerability Panic
Why is every vulnerability the worst thing since sliced bread? Here are some tips for cutting through the clickbait and FUD to see if you need to be concerned.

New vulnerabilities and issues are published at a ridiculous rate these days. I would categorize these vulnerabilities into three basic categories in order of frequency:
- Scheduled, routine announcements from established vendors.
- Actual emergencies - for at least some environments.
- Sensationalist headlines from people with an agenda - and they're using a vulnerability to forward that agenda.
Each of these is important (yes, even the sensationalist headlines), and which category they land in really depends more on your point of view than the motivations of the researcher or the company involved - generally.
Usually, these announcements can be categorized further by what you can or must do to mitigate them:
- Routine, push a patch, perhaps update a setting.
- No patch yet exists or the patch itself isn't enough, but there are mitigations you can put in place.
- THE SKY IS FALLING! THE SKY IS FALLING! Rip and replace or hopes and prayers are your only options.
Don't get me wrong, the sky does sometimes fall in our cybersecurity ecosystem, and we need to be aware of it happening, but so often it turns out that it isn't the entire sky, it's just a hunk of blue ice falling off an airplane: a rare localized event that is being covered as if it is universally important. An example of the difference between these two is readily available. Compare the July 2024 Crowdstrike outage incident to the September 2024 Yubico vulnerability announcement. The former really did have wide-ranging impacts, the latter is also extremely important, but to a much smaller subset of people and organizations.
But how do you tell which is which? How do you know if this is business as usual or an "all hands on deck" emergency?
Know Your Own Risk Situation
Sure, we can talk about this in complex terms, with lots of risk jargon, or we can discuss what it really means: what vulnerability announcements are likely to impact you, and how much damage would they do? For a company that's a pretty complicated question. For an individual that is slightly less complicated. Some guidelines that have worked for me and my somewhat complicated personal risk surface have been these:
- I focus most on systems that are Internet facing and/or don't auto-update themselves more than I do the systems that auto-update and don't talk off-network.
- I focus more on systems that store or interact with my sensitive information than ones that don't.
- I focus on defense in depth whenever possible.
So all of this sounds great, but it's still potentially quite a list. Between video streaming devices, laptops, cell phones, raspberry pis (pies?), e-readers, routers, modems, firewalls...and that's just my travel stuff. Then there are the "Smart" TVs, Blu-Ray players, more raspberry pis (pies?), desktops, NAS...they all make for a big group of things. Oh yes, and my mobile drives, physical security keys, home automation system...yeah, lots to keep straight.
But really, a lot of it is self patching. Much of it, doesn't have any real sensitive data on it, and yes that is a judgement call. So it does narrow things down a bit for me, and that's helpful. A categorization strategy can help you as well.
Know Vulnerability Scope Buzzwords
There are some words and phrases that really help me narrow down my focus when a new vulnerability is announced.
Physical Access To the Device
Whenever a vulnerability states that the attacker needs physical access to the device I get very relieved, unless it is about my door locks. That phrase is code for "people aren't going to try this against a regular person working for a regular company." Why? Because the level of effort is usually too high for the value of that vulnerability. If a malicious actor has physical access to your stuff they can probably get what they want through simpler means - if you're a "regular person."
If you're one of those VIPs who works at a VIC (Very Important Company) or perhaps a government employee in any of a number of departments, this might concern you. But then again, you're likely the sort of person who has other significant security threats to worry about.
In my world, physical access to my device might as well mean total control of it. Let's face it, a numeric pin on my phone is only so strong. A password on my laptop is only so good. But I counteract this by keeping control of my devices. Is that foolproof? No, but it's good enough for my level of security needs.
Users Are Urged To Patch Now
This one is easy. If someone is urging me to patch a system I have, I patch it. Then I move on.
I know what you're saying: Bill, what about testing? What about making sure the patch doesn't screw things up? To these questions I offer one answer: if you have an efficient, practiced, and timely routine for patch testing then by all means implement it. If not, I'm of the belief that you have a lower risk of a bad patch causing issues than of a vulnerability being exploited once it has been made public. Is that a pretty big generalization? Sure it is, but I'm writing a blog post here, not a text book, we don't have time or the attention spans for every eventuality.
Zero-Day/No Patch Available
These are the phrases that get the most attention from me. This phrase is my immediate trigger to pay attention to the story and look for mitigations I can enact. This is where I focus on the tips and tricks for preventing the vulnerability from being taken advantage of.
Gotchas
Politics, rivalries, and personal gain do show up in these alerts from time to time. Tip-offs include disclosures that complain that established companies, such as Microsoft or Google, haven't responded or haven't taken the vulnerability seriously are usually red flags. Companies like these which have established notification processes and a proven track record of acknowledging and addressing issues suddenly not doing so can be a sign that the researchers either haven't followed the established responsible disclosure process and are either intentionally trying to make a splash or are unaware of how to follow the process.
There are also those vulnerabilities that people disagree about. The recent hubbub over a "demo app" on Android devices comes to mind.
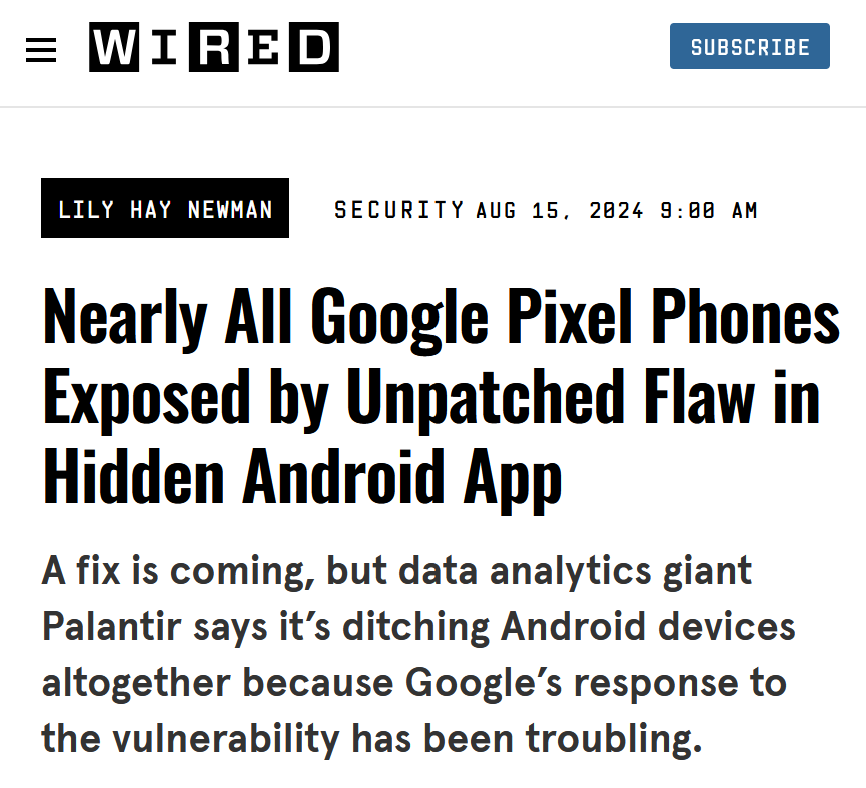
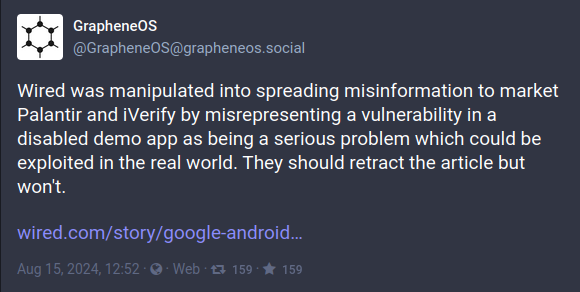
Screenshots of a Wired story and rebuttal from a 3rd party with knowledge
The app certainly isn't a good thing to continue to have on android images, but it seems that the conditions required to execute the app effectively mean that a malicious actor already has all the access they need to do nearly anything they wanted to on the device already. (GrapheneOS is a security focused phone OS that is built on the open-source version of Android and is a "Google-less" version of the OS, supporting current Android hardware. They have reason to be extremely intimate with the entirety of the Android OS, and speak from a position of direct knowledge, including their own analysis of this exact same demo app a decade ago.
These are edge cases, but they do happen. So how do you take all of this information and sift through it?
The Value of Trusted Analysts
None of us knows everything about all of these things. Many of us know "just enough" to make educated decisions at a little below the surface. But we're not alone. We have communities we trust for information. Sources we know will help sort out the stuff we're not deep experts on. They're great resources for sorting out the extremely important vulnerabilities from the "gotchas" and everything in between.
Websites like The Register, Ars Technica, and Bleeping Computer are good sources for cybersecurity information in many instances. There are plenty of others, but these are great starting points.
Many industry vendors offer great insight as well. EDR companies, incident response companies, and others often have excellent blogs - but those often go rather deep and may be too far down the rabbit hole for you.
That leaves experts. Twitter used to be one of the absolute best places for cybersecurity information and analysis. These days I really recommend Mastodon instead. In fact, the infosec.exchange instance has some great resources who have informed points of view on these issues. you could do worse than finding my profile there and reviewing my follow list for some fantastic resources in this area.
Keeping Your Head
The constant barrage of vulnerability alerts can be overwhelming. But by focusing on your own risk situation, learning some of the key phrases and buzzwords, and building a network of trusted analysis resources you can take a lot of the stress out of these warnings while still acting on the important ones. Advice you can use in your personal life, as well as if you're charged with securing your organization.

